You may have heard of DMARC, and you may have even copied and pasted a cryptic DMARC value into a text record for your domain, but that’s really just the beginning. If you’re not already familiar with DMARC, that’s alright. There’s a great DMARC guide available from Postmark that explains everything. So, if you need some context start there.
The simplest explanation for DMARC is that it’s a way to monitor sources that are sending email using your domain and a way to explicitly tell how ISP’s to handle email from your domain when it’s not authenticated. That’s the part we’ll talk about today.
When you set up a DMARC policy, you add a TXT entry (Figure 1)
to your domain at _dmarc.domain.com. The value for that entry looks something like this:
v=DMARC1;p=none;pct=100;rua=mailto:dmarc-reports@domain.com; In particular, we’re going to focus on the p=none;pct=100; portion. The p stands for ‘Policy’ and tells ISP’s how to handle emails that fail to align with DMARC. You have three options for that value: none, quarantine, and reject where each is increasingly aggressive. With none, they won’t do anything. They’ll send reports but otherwise will process the email like any other. Using quarantine tells them to put it in the spam folder, and reject gives the green light to discard it entirely.
The second value, pct stands for percent and tells the ISP what percentage of the emails they receive from your domain they should filter according to your declared policy. So, if you set pct=50, then ISPs will examine 50% of the emails that appear to be from your domain. Then, if within that subset of emails they examine, they find any that aren’t aligned, they use your specified policy to handle them. That could mean doing nothing, putting them in the spam folder, or outright rejecting them.
Getting to a policy of rejecting 100% of emails that aren’t aligned is an admirable goal, but naturally, it’s complicated. The catch with implementing your DMARC policy is that you likely have some legitimate sources of email that wouldn’t align with DMARC. That could be caused by providers that don’t support the necessary authentication, someone may have forgotten to set it up, or someone could have set it up incorrectly. So, with any DMARC policy, you’ll want to start with p=none;pct=100; with the goal of eventually getting to p=reject;pct=100.
So how do you do that safely without accidentally blocking legitimate email? Very slowly, but you’ll need a little help first. Once you’ve setup DMARC, ISPs will send you reports about the activity they’re seeing from your domain. However, they send it via XML, and it takes some work to understand it. Fortunately, there’s a variety of DMARC reporting tools out there. I highly recommend Postmark’s free DMARC tool. They’ll collect the XML reports and send you a detailed break down once per week. The downside is that it’s not quite as advanced as some of the other paid tools, but it works incredibly well.
Once you start receiving reports, they’re organized into four key sections. (Figure 2) First, you’ll see a summary of the quantity of emails processed during a given period, what percentage were aligned via either SPF or DKIM, and what percentage were not aligned. Below that, you’ll have a few sections. “Your Sources” shows the sources of email that are aligned. These services should be familiar to you.
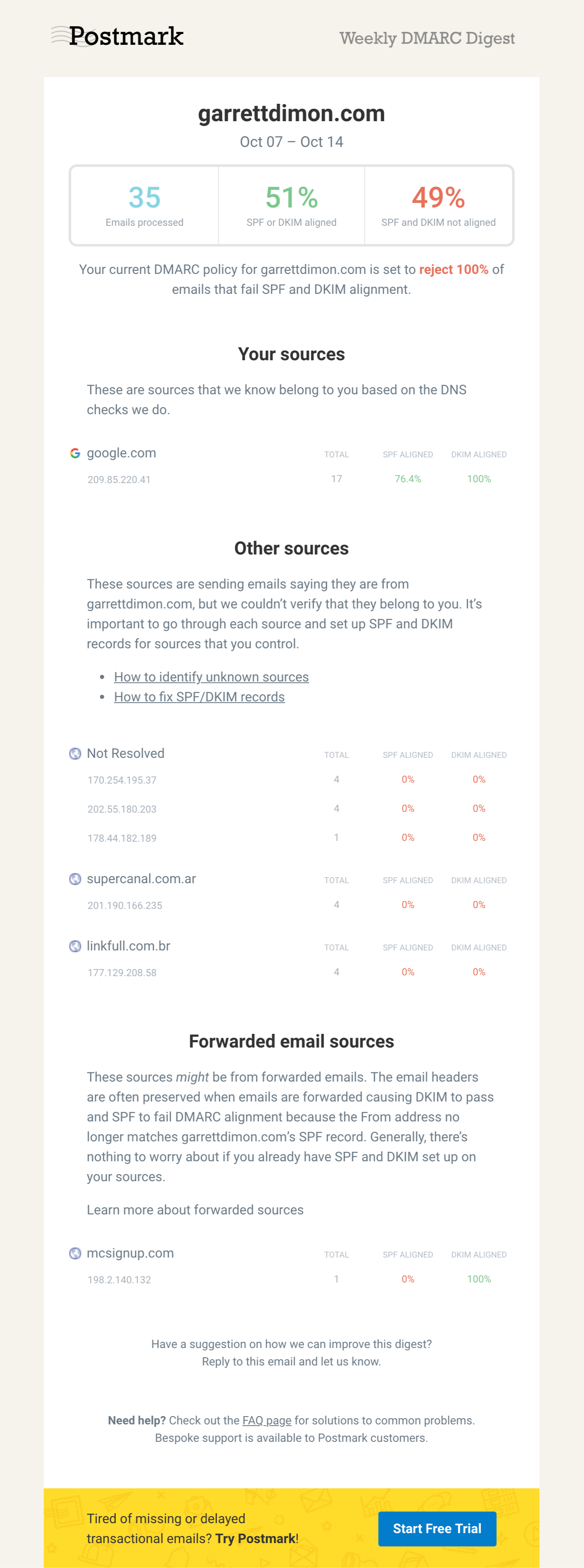
A sample weekly DMARC report from Postmark’s free DMARC service
↩︎Next, you’ll see “Other Sources” where alignment failed. In these cases, you may recognize some of the sources. When you do recognize one, you’ll want to go and ensure that you have DKIM and/or SPF set up so that it will be aligned in the future. For other sources you don’t recognize, it’s likely they’re the malicious emails that you’d eventually like ISPs to reject completely.
When you have “Other Sources” where it’s not immediately obvious what the source is, there’s no easy way to figure it out. It requires investigating the IP address through search engines and other methods. It may never be obvious what a given source is. Just bear in mind that most legitimate sources will either show up with a domain or otherwise quickly surface results from search engines. If the volume is incredibly low for a given source, you probably don’t need to worry about it.
At the very bottom, you’ll see “Forwarded Email Sources.” These represent the situations where an email likely didn’t have full DMARC alignment because the SPF record was broken in the process of an email being forwarded. You generally don’t need to worry about these as the failure is probably outside of your control. Moreover, as long as there’s a partial pass via DKIM, that’s good enough.
In the beginning of locking down your DMARC policy, you’ll want to try and think of every legitimate service that you or your company have enlisted on your behalf. Are you using email newsletter software? Does your application send transactional email? Have you set up your payment processor to send notification emails on your behalf? Then, make sure you set up authentication for all of the valid sources.
Over time, as you regularly receive reports and set up your authentication for legitimate sources, you’ll reach a point where you can feel confident that all of your legitimate sources are properly authenticated. There’s no specific timeline that’s right for everyone. You may only need a week for a tightly controlled domain with low volume. Or, at a large company with many teams sending from the domain, you may need months of monitoring and communication. Either way, at some point, you’ll be confident that you’ve done everything. Then you can start to think about making your policy more aggressive. When you do this, you’ll want to make sure your team is aware. If emails start to go missing or end up in spam folders, your customer support team will hear about it. So it’s important for them to be on the lookout in addition to you continuing to monitor your reports.
You can take a methodical approach and switch to a quarantine policy with 10% and then increase it by 10% every week. Or, you could try quarantine policy at 100% as your first step if you feel really confident. After some time without any issues for your legitimate email sources, you can move to a reject policy. Bear in mind that a reject policy will make it incredibly difficult to troubleshoot lost emails. You’ll still see the aggregate numbers in your reports, but that’s about it. Similarly, setting up new email services for the domain means they won’t work at all until they’re properly aligned. So it’s important to continue to monitor those DMARC reports.
This can be a tedious ongoing effort, but protecting your domain and your brand is important. DMARC puts some of that power back in your hand. It requires effort and research, but locking down your domain and potential email sources will only help protect your delivery reputation. It’s also the first step towards being able to use BIMI, but that’s a separate topic.